My Facebook and Twitter feeds are infested now with news articles about the cyber espionage campaign dubbed as “Dark Caracal” involving the Lebanese Directorate of General Security, and so far I have seen all kind of comments from people who are oblivious about this revelation to others who now believe that every single Lebanese mobile phone is subject to the espionage campaign. So there you go, everything you need to know about Dark Caracal.
What?
Mobile security firm Lookout, and digital rights group Electronic Frontier Foundation, released a report yesterday attributing a global cyber espionage campaign that they called “Dark Caracal” to the Lebanese Directorate of General Security.
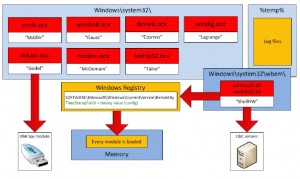
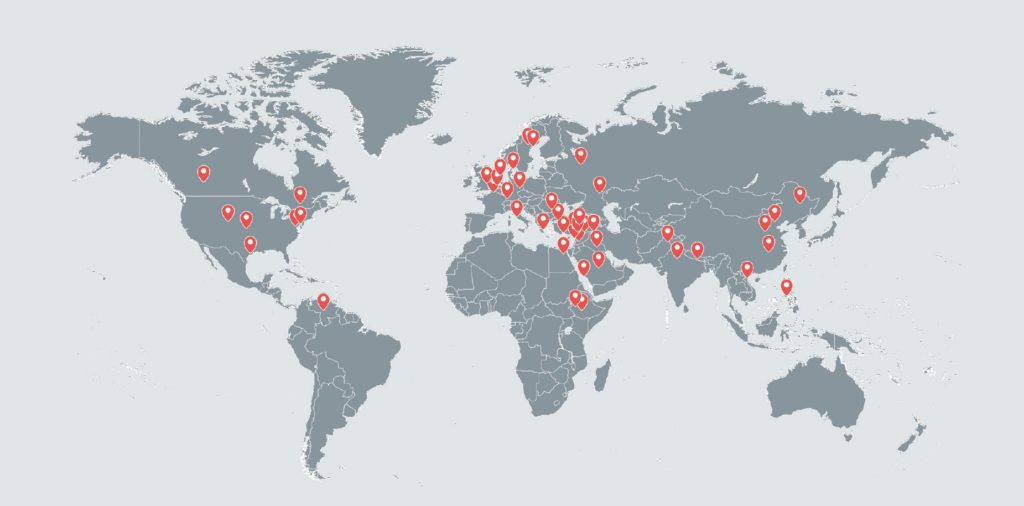
The attack carried out by the hackers apparently seized control of thousands of Android phones from around 21 countries and resulted in stealing hundreds of Gigabytes. Researchers were able to gain access to one of the servers used by the hackers and found that the stolen data included: SMS Messages, Account credentials, WiFi details, Call records, Bookmarks and browsing history, Messaging apps databases (WhatsApp, Telegram…), Contacts, Installed Apps, Personal documents, Images, Voice recordings, and Listing of the phone storage content.
It is worth noting that all attacks targeted Android phones and there was no evidence of targeting iPhones. On the other hand, files stolen from personal computers included full backup images of iPhone mobiles. Moreover, I found it a bit weird that users from neither Israel nor Iran were victims to this campaign.
How?
In terms of hacking, the attackers did not utilize very sophisticated techniques to control the phones, they actually launched several campaigns that consisting of sending phishing links and fake applications to their victims in order to lure them into installing some malicious applications on their mobiles and computers which in turn uploaded their personal data to some remote server controlled by the hackers.
As to how these hackers were busted, the researchers claimed that they spotted several testing devices that were used by the hackers themselves to test their malware, and those devices had one thing in common which was a WiFi network called “Bld3F6”. Upon investigating a little, they were able to identify that this WiFi network was located very close to the General Security building in Mathaf.
When?
The researchers found that the campaign was first launched in 2012 and was still active at the time of publishing their findings.
Are we all compromised?
Certainly not. Some people made it seem like the General Security have super powers now and are able to infiltrate all our devices. If you use trusted WiFi networks, double check each link you see on the web before clicking it, and make sure to install legitimate apps only on your mobile, then you are most probably safe.
Conclusion
I have mixed thoughts about this. Is it ethical to spy on people? Definitely not, but all governments do it anyway, and assuming that the General Security is really tied to this cyber campaign then our government is no different. I’d like to believe that what they’re doing is probably protecting us from terror attacks, but I also value personal privacy and would feel outraged if I knew someone had access to my personal data…
Anyway, if you feel like reading more about Dark Caracal, you can find more details in the 49 pages report prepared by Lookout and Electronic Frontier Foundation here. One thing that I thought the report lacked was more details on how the researchers gained access to the servers utilized by the hackers, otherwise it is quite informative.